There is close integration between Google Calendar and other Google apps. For example, Gmail users who also subscribe to Google Calendar can have the events mentioned in emails automatically populated in Google Calendar. This feature is unique and offers the utmost convenience to users, which underlines the reason for the popularity of Google Calendar that can serve many functions of a personal assistant. Similarly, there is close integration between the calendar and other Google apps.
But along with the convenience comes the threat of hackers and cybercriminals who are exploiting the popularity of both Gmail and Google Calendar. They target users for accessing their credential related information by hacking into their systems and luring them to divulge information by using various tricks. This has been the finding of Kaspersky’s security researchers. Users must take guard to protect their privacy and personal information that remains exposed to the risks of falling into the wrong hands.
What is the attack like?
Cybercriminals bank upon the tight integration of various Google apps and services to carry out malicious attacks. They access personal information that can have significant business prospects on the dark web. According to calendly.com, the attacks are nothing short of a sophisticated scam; the primary target of the attack is Gmail users who are victims of unsolicited and malicious Google Calendar notifications. The design of the calendar app allows anyone to set up a meeting with you. The design of Gmail, which receives the notification of the invitation, is such that it tightly integrates with the calendar functionality.
On sending a calendar notification to any user, they receive it as a pop-up notification on their smartphone. The cybercriminals create their invitations to include a malicious link to take advantage of the trust that develops due to the user’s familiarity with notifications. Security watchers and researchers have observed that attackers consistently use the technique for a month to trick users with phishing links that lead to sites that facilitate stealing credentials.
The attackers populate the topic and location field to deceive users by announcing a fake questionnaire with financial incentives. They also create fake online polls to lure the victim to follow the malicious link that can be useful for them to collect credit card details and bank account details, which are the primary targets. The non-traditional technique of attack allows criminals to get around the fact that people are aware of by clicking on suspicious links that can be deceptive.
More than phishing
The technique of duping users described above is more than plain phishing. According to security experts, the technique is the gateway for opening a whole range of social engineering attacks. The risks are much more than just stealing personal information because they can use it to gain access to a building. For instance, you can use a calendar invite to set up a face to face appointment for building maintenance or an interview with someone on some pre-text, which could help in physically accessing secure areas. The danger is much beyond the realms of phishing attacks, although it looks much similar.
How to mitigate the risk?
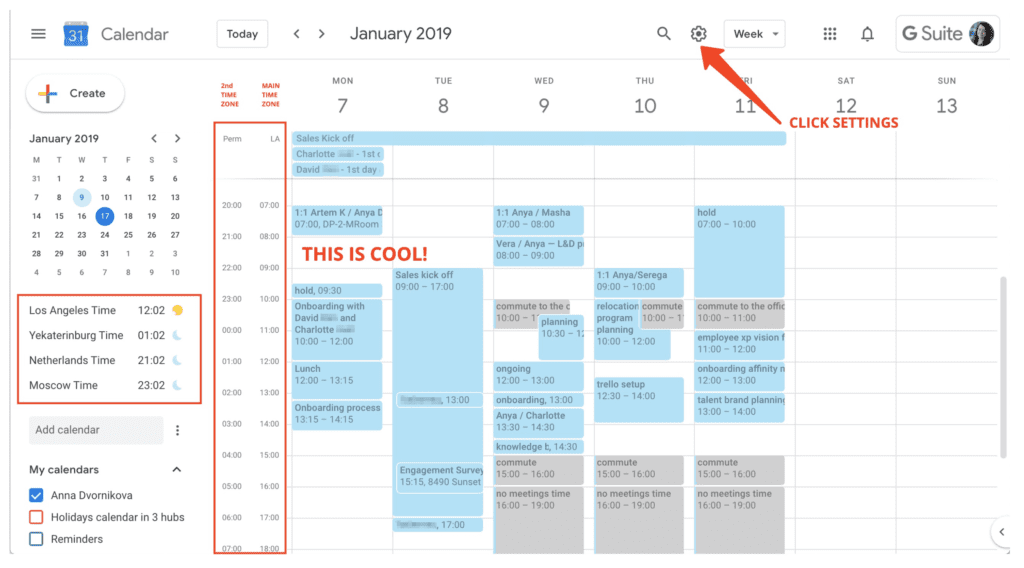
One thing that calendar users must keep in mind is that the more convenience they seek, the higher are the chances of inviting problems. Use automation with discretion is advice from security experts. They recommend turning off the function of calendar invitations automatically. To deactivate the functionality, go to the Google Calendar menu and then to ‘Event Setting’ under it. To disable the function ‘automatically add invitations,’ enable the function ‘only show invitations to which I have responded.’ Moreover, uncheck the ‘Show declined events’ in the View Options section.
It might happen that the above method does not suit you because it seems impractical, which can happen to many other users who rely on this type of schedule. In such a case, there is another way of tackling the problem. You must be extra careful and vigilant in examining every invitational email that you receive. If it feels unusual, wrong, or weird, then verify the origin of the email and ask the sender if they have sent it. Relying on your brain could give better results than relying on technology to detect phishing emails that can have far-reaching effects on your privacy and security.
A third way to ensure safety against phishing is to rein in your curiosity and give up the habit of clicking on every mail attachment or link you encounter. Rely on your gut feeling to decide which attachments to open and discard outright and delete without a second thought. However, it is best to pay heed to the first piece of advice and use the calendar settings to stop adding invitations to your calendar automatically.
Google’s reaction

What was Google’s reaction to the issue that was brought to their notice way back in 2017? Google has always worked for offering the best user experience, which remains non-negotiable for the tech giant. When informed about the vulnerability, Google accepted it and responded by adding an option for disabling the functionality. However, the action was not fool-proof, as proved by security researchers who were able to find a way around it and brought it to Google’s notice.
While replying to the researchers, Google admitted that it was plain eyewash to soothe the nerves of users as it did not have any intention of fixing the problem because of wider ramifications. Making any change to the functionality would result in major drawbacks for the functionality of legitimate API events with Google Calendar.
Against this backdrop, it becomes clear that self-help is the best help. Users must reduce their over-dependence on automatic functionalities as much as possible when using Google Calendar and stop using the functionality of automatic adding of events to the calendar by extracting it from Gmail. Instead, scrutinize every mail invitation and take the best decision in dealing with it either by accepting or rejecting it by judging its genuineness.
 Imagup General Magazine 2024
Imagup General Magazine 2024



