The new millennium represents a turning point in various areas of development of society and civilization, in which digital media have perhaps the greatest role. In the visual culture of the mass media, their performances determine the understanding of the world, the sense of personal identity and gender, style, and way of life.
In this way, new digital technologies have a significant role in the process of improving the quality of child protection. The basic preconditions for the efficient use of digital media for this purpose are the existence of IT knowledge of the child’s parents/guardians, as well as educational institutions.
So that the child, in addition to the primary family and the educational institution, got a third member in the educational process. This applies to digital technologies and their power of protection. We’re sure you’re all familiar with online tracking apps, but this isn’t the only way. Read on to find out the two most important roles of digital technology in child protection.
1. The role of digital technologies in the protection of kids through the influence of parents

This is possible so that the parent has an absolute insight into the child’s movement on the Internet and outside it. This can be done with a few things:
Tracking Applications – Today, there are a large number of applications that do a great job. Their application is wide, so they can be installed on a phone, computer, tablet, and smartwatch.
Each of them has different tracking variants. For example, one application can listen to a child by making the following happen: If the child does not answer the call, parents can turn on the microphone and hear everything that is happening around their child. The application allows the child’s movement to be monitored in detail, so you can know at any time when he entered the house and left the house or other places.
Also, certain applications allow you to follow the child at the moment. It can be installed secretly. Personal data is kept in strict compliance with legal regulations. The service uses the child’s GPS phone, on which it works in GPS location mode. Read more here about how that function.
The application that enables the SOS button is a complete hit with parents. This is very popular due to its extreme practicality. The child communicates with the parents in this way, and in case of an emergency, he can press the SOS button. The alarm signal then automatically reaches the parent’s phone.
Developing adequate communication on the Internet – The Internet is a great thing. Only from the previous text, we can conclude that its options are unlimited. By using it for the right purposes, we can achieve a lot.
There is no doubt that the need to develop adequate communication on Internet prevails. This refers to good behavior on the Internet, ie. behavior without threats, insults, and belittling of peers and other persons. This can be a very powerful weapon when it comes to fighting against peer violence.
Creating a child’s personal work environment – In order for this impact of digital technologies to be successfully realized, it is of course necessary for parents to be in constant contact with their children, to listen to them and to talk to them about online activities.
They help their children in case of doubts or problems, especially if they come across inappropriate content or inappropriate communication. The safest solution is to create a personal work environment, in which Internet access is limited to certain locations.
The computer is equipped with this procedure and protected by programs and filters. Access to the child is restricted to pre-determined locations in the presence of an adult.
2. Detection of potential crimes

This is definitely the most responsible role of digital technologies in child protection. The very rapid development of information systems has posed a great challenge to the legislative, administrative, and other state bodies, as well as to the entire international community, to regulate this area with legal regulations. Addressing privacy and security issues through electronic communications requires a comprehensive approach, involving a wide range of stakeholders, and reconciling many, often different needs and interests.
Absolute dependence on computers, networks, and the Internet as you can see has its great advantage. We are surrounded by potential danger on a daily basis. Thanks to the authorities who are well acquainted with the functioning of computers, computer programs, and computer networks, security vulnerabilities that can lead to criminal acts are eliminated.
The authorities are successfully using computers, and this is their advantage in knowing the technology of computer operation and programming in order to achieve the goals. Some examples of these procedures:
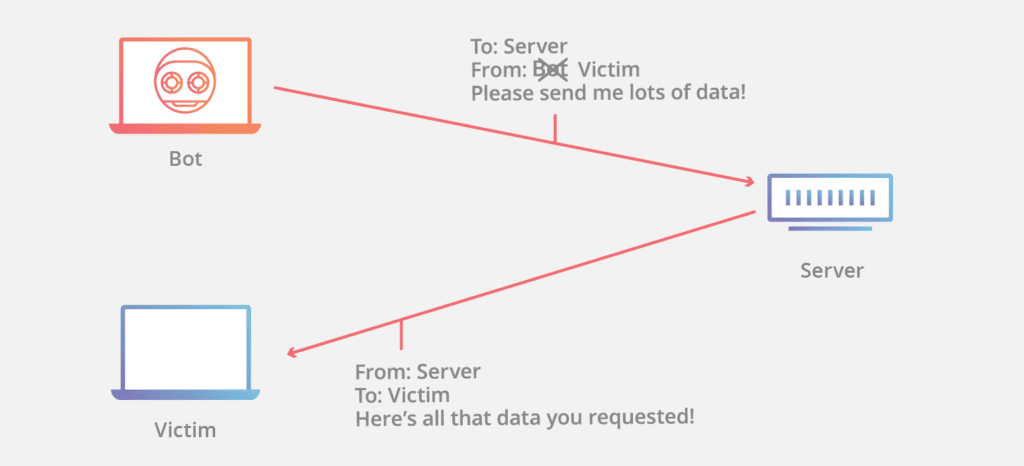
- IP Address Spoofing – Forgery of an IP address is an attempt by the authorities to present your computer or some data from the “external” network as if it came from a computer whose IP address is part of the address range of the internal network.
- Back Door – We find the “back door” in a networked environment, ie when a program is installed on a system that will allow an unauthorized person to access information and resources on that network.
- Network Sniffing – Applications can be used that “listen” to all traffic coming to the network card (NIC) and use this information to access valuable data (usernames, passwords, entire messages …). The following programs are popular: Kismet (used to listen to wireless traffic),… Keystroke logging is a method of recording everything the user types. The principle is to install an unidentified program on the computer, which will record everything that the user types on the keyboard, and later make it available to a third, uninvited person.
- “Viruses” – Computer viruses are programs that are capable of infecting and copying to a computer without knowledge. In order for a virus to run, it must be started, and in order to “infect” other computers, it must be transmitted via some medium (DVD, USB Memory Stick, shared, shared network drives).
- “Worms” – Unlike viruses, “worms” use a weakness, a “hole” in the system to replicate, without any user intervention. They usually open communication on one of the TCP ports to take control of the computer (Back door, type of attack).
Conclusion

Since digital technologies are an indispensable part of our lives, in addition to the positive ones, there can also be negative sides. We tell you again, be careful. We hope that this text has brought you closer to the importance of the Internet and its various options and that you will continue to monitor the safety of your child.
 Imagup General Magazine 2024
Imagup General Magazine 2024



